Michael
Pipe
| LOCATION: BEDFORD
| PHONE: +44 7960219451
| EMAIL: PADDY@MICHAELPPIPE.CO.UK
| PREFERRED NAME: PADDY PIPE
Recent graduate of the University of Kent achieving a First-class classification in Computer Science with a year in Industry. I am looking for an interesting start to my career in IT, ideally in development with a company that is focused on the progression of its employees.

Experience
Infrastructure Engineer
Wates Group
August 2016 - August 2017
As part of my degree I completed a year in industry at Wates as an Infrastructure Engineer. My main focal point was Line of Business application support which entailed dealing with issues, changes and problem tickets raised within the ITSM tool. My role also consisted of other duties such as;
- Technical support on projects
- Problem management and Major Incident Reporting
- Process automation
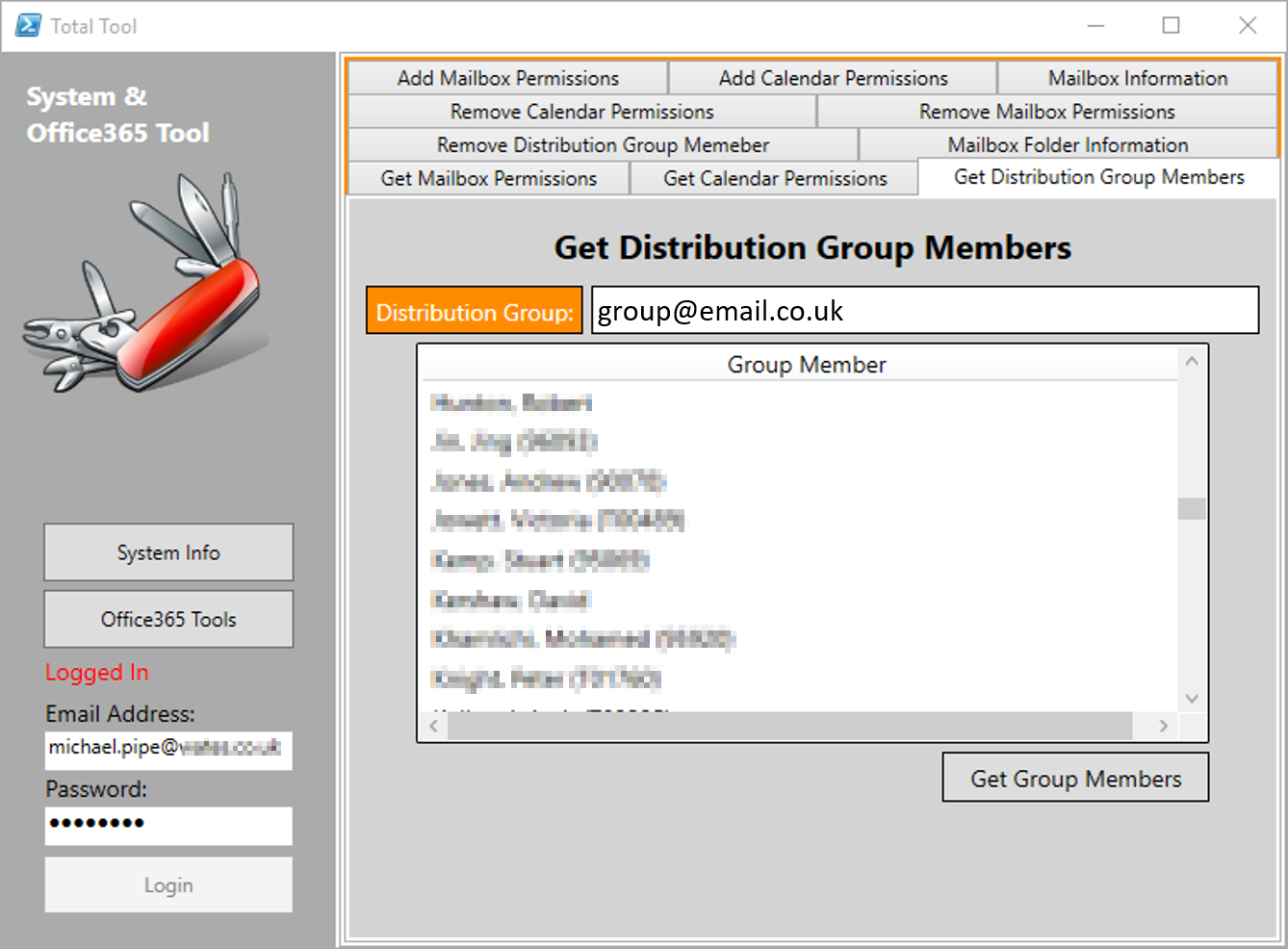
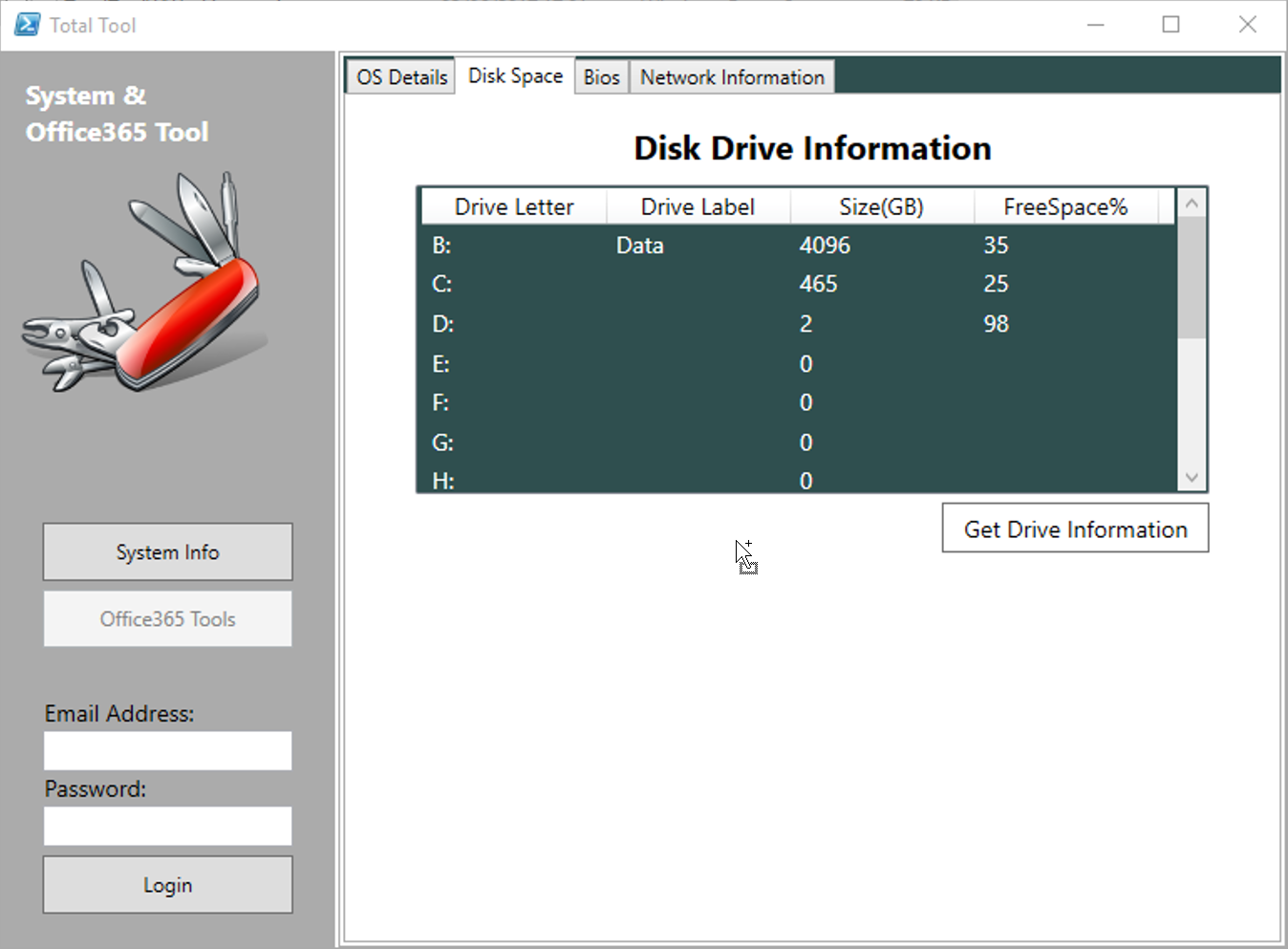
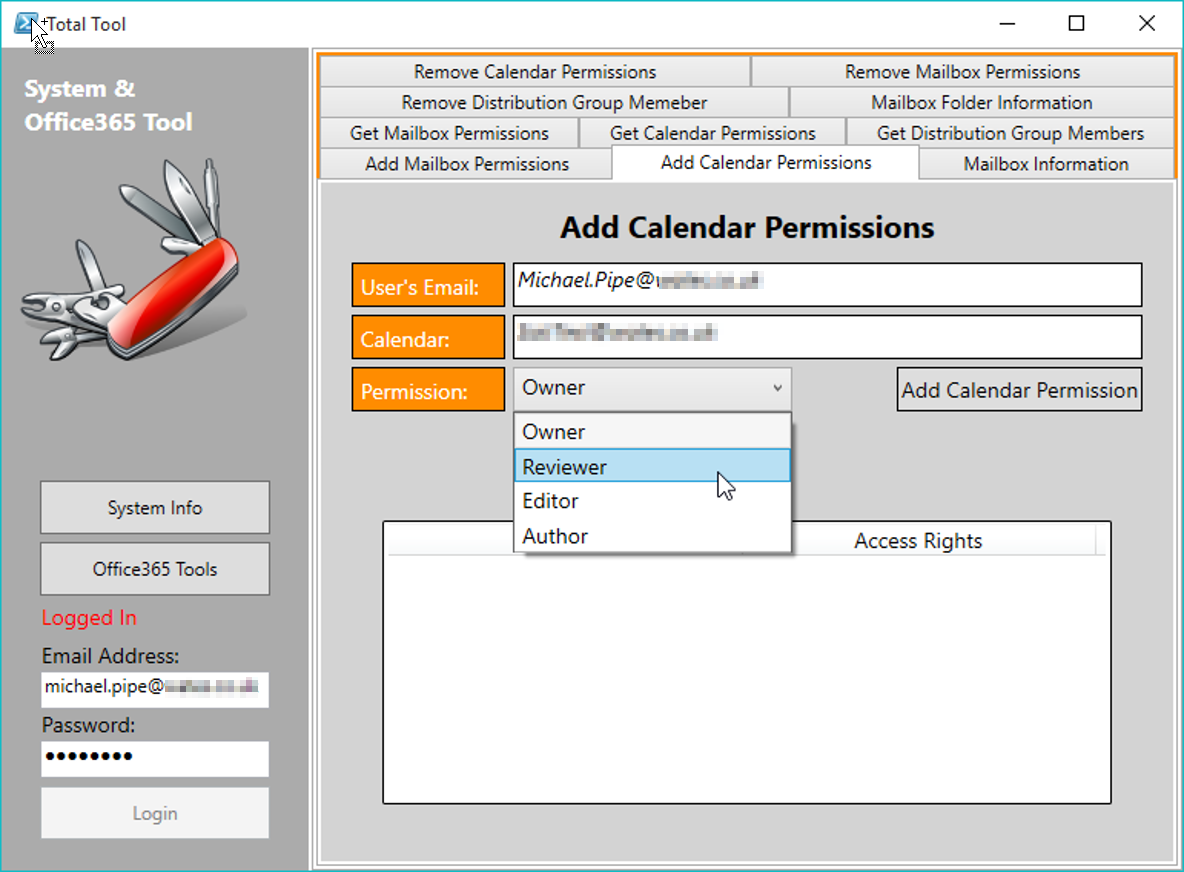
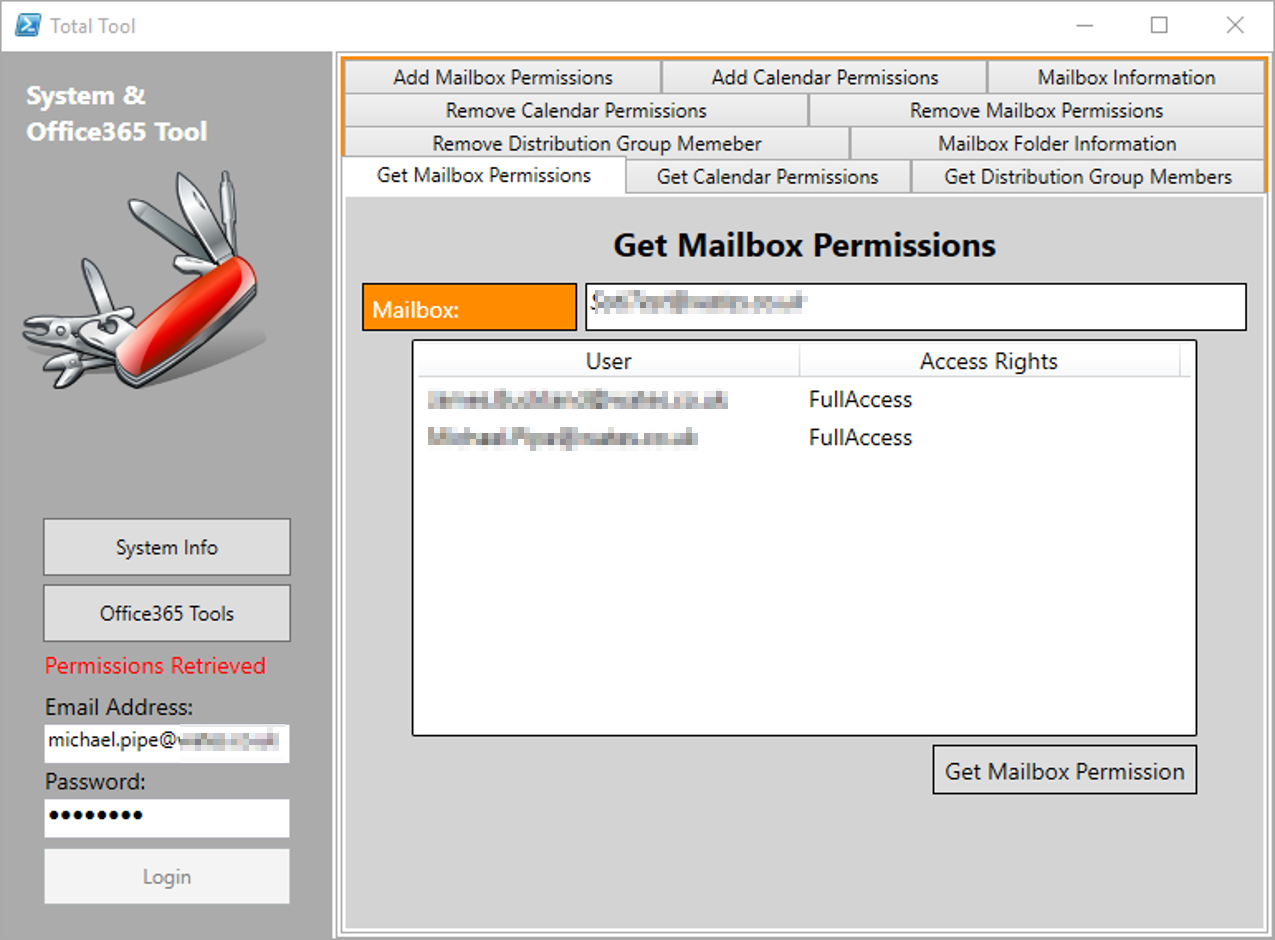
- Development of an Office365 Exchange Admin Tool (see produced)
Government Funded Cyber Security Research Intern
The University of Kent
July 2015 - September 2015
During the summer of my first year at Uni I had an 8-week research internship where I looked into Threat Analysis in Self-Adaptive Authorisation Systems. This internship was completed as 2 weeks’ remote work where I had daily meetings with my project leader and then 6 weeks based at the University of Kent. The internship consisted of researching and reading papers relevant to the topic as well as creating a simulation for anomaly detection using data collected from an online game that emulated insider attacks on a system.
Education
The University of Kent
Computer Science with a Year in Industry BSc (First-class honours)
September 2014 - June 2018
| Module Name | Achieved Percentage |
|---|---|
|
Web Development
This module covered HTML, CSS, php and JavaScript as well as AJAX and frameworks such as CodeIgniter and JQuery.
|
85% |
|
Programming Language: Application and Design
...
This module came in two halves. The first half covering multiple languages such as Java, OCaml and Haskel to show how different language types (OO/Functional/Combination) can be better suited to different applications. The second half describing the conceptualisation of programming languages from a design aspect, touching on lambda calculus and language rules.(see produced)
|
83% |
|
Internet of Things
...
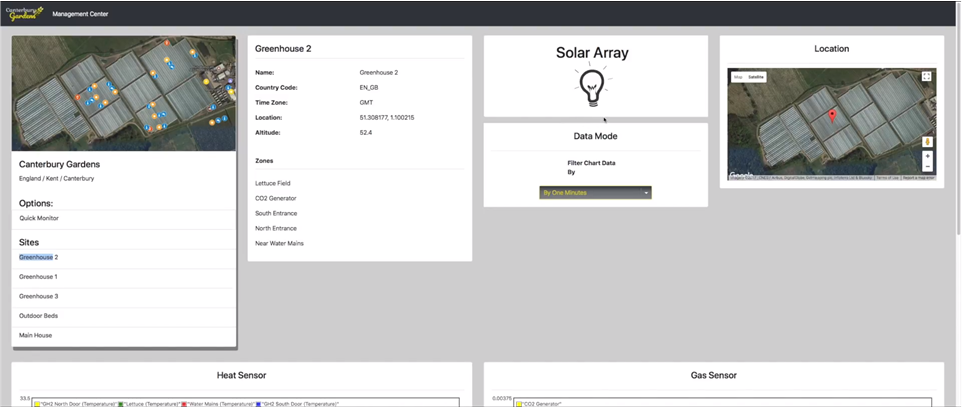
In this module we took an ARM based microcontroller and using C++ we utilised different sensors in order to collect data from real sources, uploading sensor results to a dedicated server. We were then tasked with producing a dashboard where we used HTML, CSS, JavaScript, Bootstrap and pre-provided APIs for data aggregation of multiple sensor readings.(see produced)
|
83% |
|
Database Systems
...
Data modelling, Normalisation, SQL, Relational databases, Temporal databases, noSQL, Object-Relational databases and Inheritance
|
83% |
|
Intelligent Systems
...
We studied different search algorithms such as iterative deepening, depth-first, depth-limited, uniform-cost, best-first and A* and how these can be used in puzzle solving and problem realisation. We also covered game theory and related topics such as the minimax theorem and alpha-beta pruning. Finally we looked at neural networks, training perceptron’s with learning rules and backpropagation.(see produced)
|
78% |
|
Final Year Project
...
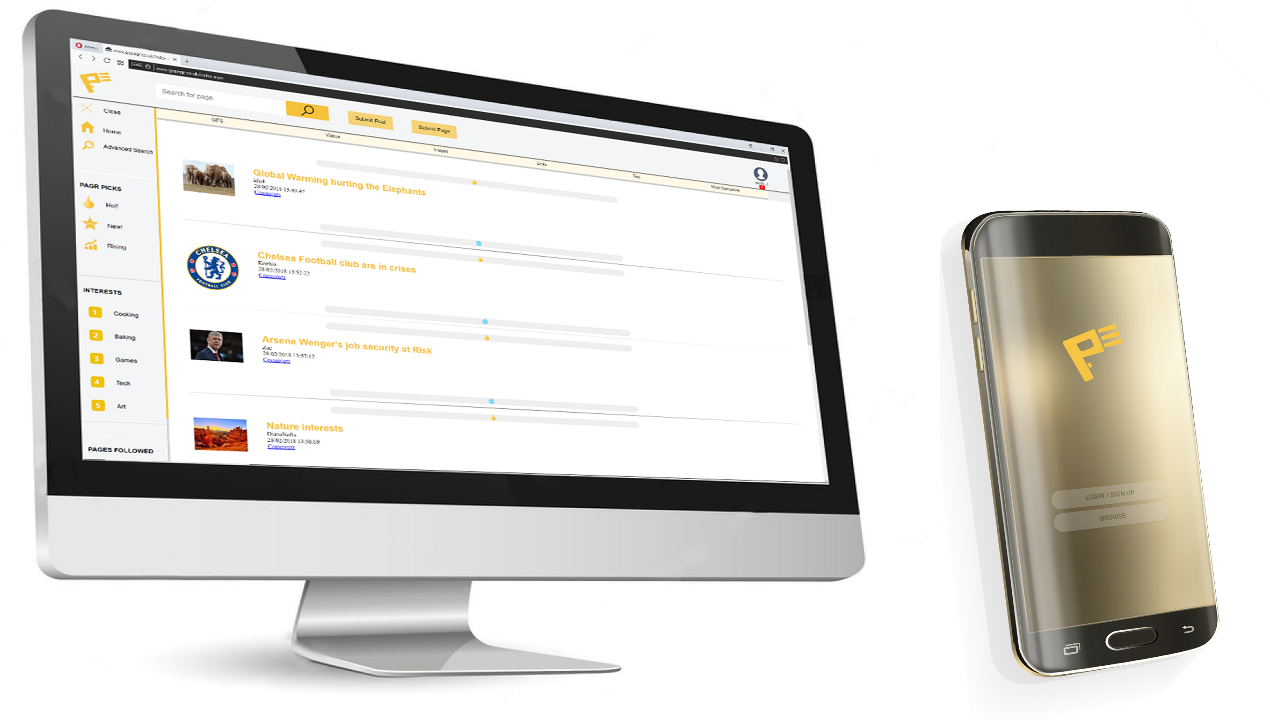
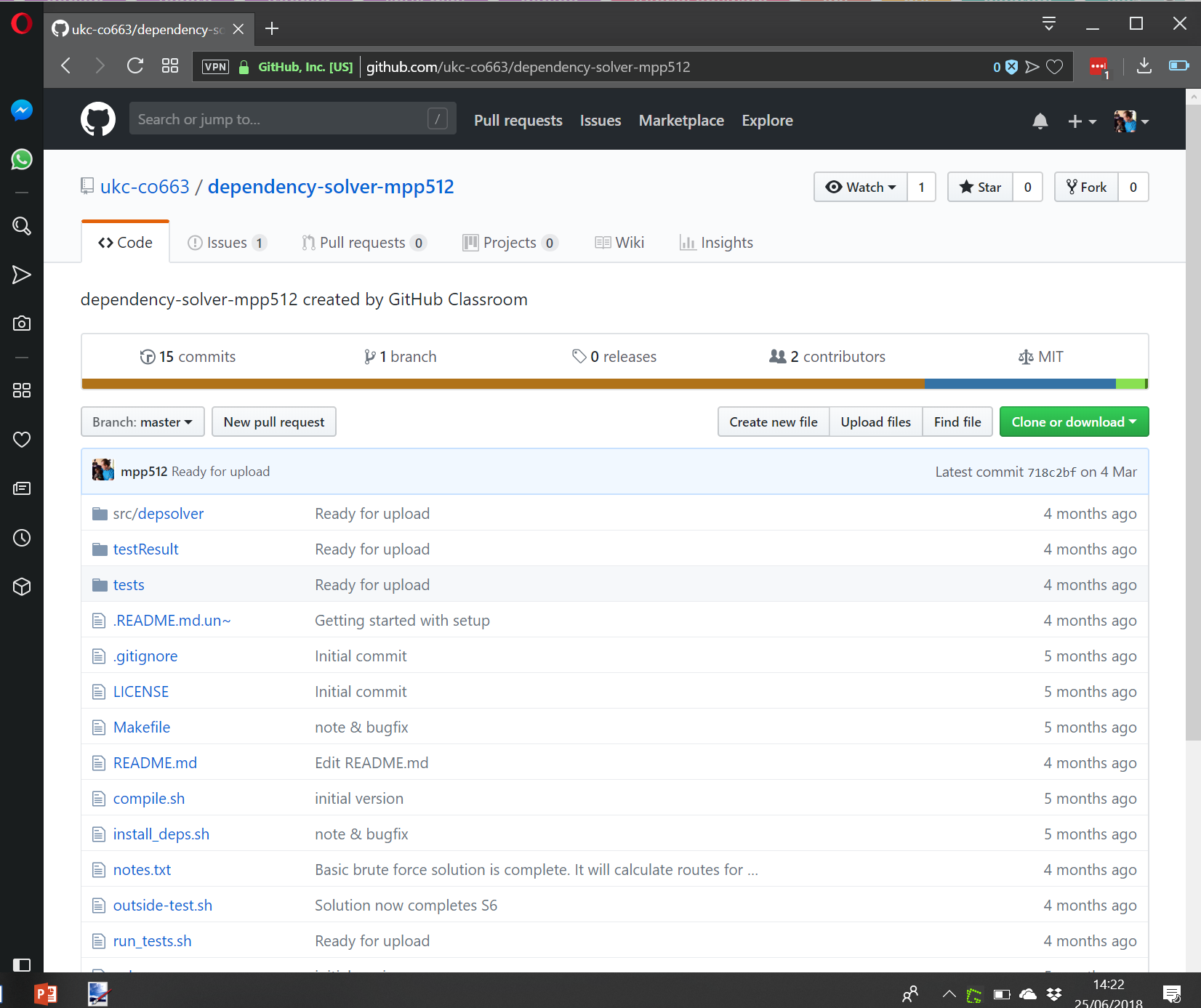
My final year project was to take the conventional forum style website, looking at websites such as Reddit, and to improve on the issues we felt were present. Working in a group of 5 we decided that we would improve on the social aspects of the site and try to improve the voting system so that the score which a post could get wasn’t incorrectly or unfairly judged. The final outcome of the project was a hybrid social network planned, developed, tested and improved throughout the year. We had two front ends, one web based and the other native Android, both backing onto the same SQL backend. The web front end was developed using HTML, CSS, JavaScript, APS.NET and used C# for the backend. The Android application was Java using http requests to php SQL query scripts as an API. (see produced)
|
75% |
|
Functional and Concurrent Programming
...
Fundamental concepts of functional and concurrent programming using Erlang. How evaluation operates, side-effect-free programming, communication and synchronisation. Using the inherently recursive style of functional programming languages to solve regular problems assessing through typical problems such as the dining philosophers.
|
75% |
|
Computer Security and Cryptography
...
This module covered a number of cryptographic algorithms used by different ciphers and the weaknesses they included. We were tasked to target these weaknesses by decrypting multiple different cipher texts. We covered authentication, both symetric and asymetric as well as security concepts.
|
70% |
Wootton Upper School
A-Levels
September 2011 - June 2014
| A-Level | Achieved Grade |
|---|---|
| Techology | A |
| ICT | B |
| Geography | C |
Produced
Skills
Web Development




OO-Programming

Other









Interests